.svg)

Verified Threat using Agentic AI
Discover with Red Team simulation, validate risks and Automatically Remediate



Verifiable Threat Data Features
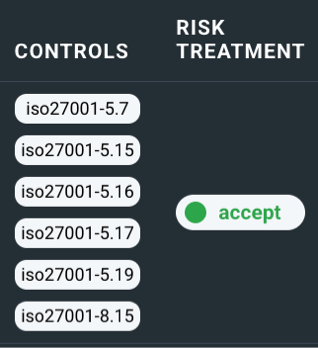
Evidence Based Cybersecurity that maps into your existing ISO 270001, SOC 2, & NIST Cybersecurity Framework
Attack / Breach Simulation
Agentic AI allows for simulation of multi-vector attack types that are often not spotted by traditional means
Clear Reporting and Threat Intel
We show the clear threats, mapped into the relevant Cybersecurity standards.
Multi-Functional Team
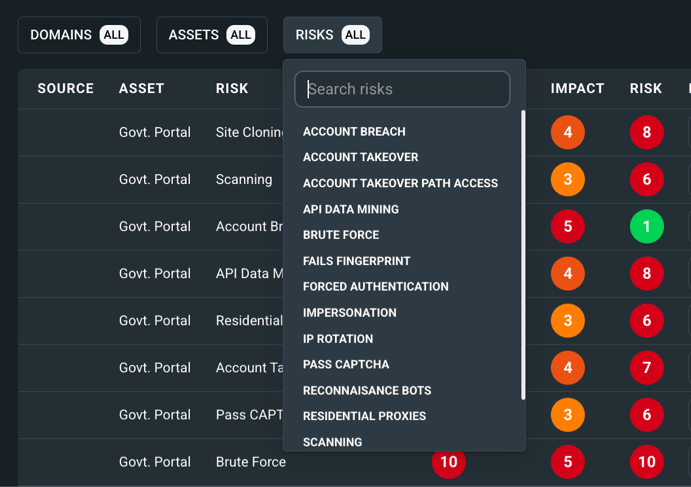
Our dynamic risk register based framework allows all stakeholders to collaborate as a multi-functional team, across Senior Leadership, Policy, Cybersecurity teams, Compliance and Risk Teams.
.svg)
.svg)
Seamless Integration Tools
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod
Customer Satisfaction
How We Help Businesses Like Yours Protect.


“We could immediately see vulnerabilities that had not been exposed with standard pentest tools, and we loved the integration with ISO 270001 to clearly show the risks in the risk register.


“We used to spend a lot of time on log analysis and identifying risks. VerifiedThreat has saved us a ton of time and effort, and allows us to auto-remediate many of the risks all with one setting. Amazing. "


"The problem with so many Cybersecurity tools is they just give out more alerts and noise. VerifiedThreat does what is says, and only presents actual threats which are proven. Massive win for me and the team. "


"Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. "
Simple, scalable pricing.
No extra charges. No hidden fees.
Fortress
Seat per month, 1 seat max, 1 domain only
.png)
.png)
.png)
.png)
.png)
Sentinel
Seat per month, 2 seats max, 5 domains
.png)
.png)
.png)
.png)
.png)
Guardian
Seat per month, 2 seats max
.png)
.png)
.png)
.png)
.png)
.svg)
.svg)



Frequently asked questions:
How We Help Protect Businesses Like Yours.
Who is your target audience?
We are aimed at small-to large corporate businesses who need to have verified risk analysis to help prevent attacks. For smaller businesses, this will provide the missing red team intelligence, and in larger companies our massive scale and auto-remediation makes the platform invaluable.
How does it work?
We send out intelligent AI agents to use tiny amounts of data to look for vulnerabilities across your digital estate. These agents are smart and have the situational awareness to leverage one vulnerability and use that to their advantage. Simulating the cyberattacks with real-world methods used by actual hackers allows the agents to spot the weakest link and automatically use the AI tools to prevent the potential attack.
Is this just a fancy pentest?
No! The way VerifiedThreat works is very different from a pen test. Pentests are heavily reliant on pre-existing threat data , and can't dynamically learn and adapt from their knowledge of your own unique platform. VerifiedThreat monitors continually, and is adaptive. Standard pentesting is very limited in comparison.
How do you integrate with standards?
We automatically map the verified threats discovered to the relevant cybersecurity standards, so that you see which standards are affected by the risk and how the risk can be addressed and fully mitigated. The risk register is automatically managed.
Who can benefit from VerifiedThreat?
Key stakeholders are the DevOps, CyberSecurity, compliance, and risk management teams.
Blog & News
Stay Up To Date

.svg)








_11zon.webp)

.webp)